In the ever-evolving world of cybersecurity, businesses
are constantly faced with the challenge of protecting their networks, systems,
and sensitive data from a wide range of threats. Traditional security measures
like firewalls and intrusion detection systems (IDS) are essential, but they’re
not always enough to detect and mitigate more advanced threats. To truly stay ahead
of cybercriminals, businesses must deploy innovative and proactive security
solutions.
One such innovative solution is honeypot technology.
CODELANCER CYBER SECURITY AND FORENSIC PRIVATE LIMITED offers
cutting-edge Honeypot Services that allow organizations to actively
engage with and trap potential attackers. By deploying decoy systems designed
to attract hackers, honeypots provide a wealth of valuable insights into attack
techniques, motives, and vulnerabilities.
In this blog, we’ll explore what honeypots are, how they
work, and why CODELANCER’s Honeypot Services can be a game-changer for your
organization's cybersecurity strategy.
What is a Honeypot?
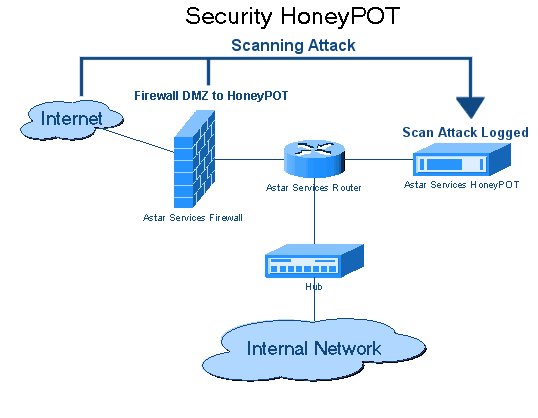
A honeypot is a cybersecurity technique that
involves setting up decoy systems, applications, or networks that are
intentionally vulnerable or unprotected to attract and deceive cybercriminals.
These systems appear to be legitimate targets, but in reality, they are
isolated environments designed to monitor and record the actions of attackers.
Honeypots serve several purposes, including:
When hackers attempt to breach a honeypot, the activity
is logged, providing cybersecurity teams with valuable data that can be used to
strengthen defenses, improve incident response, and create more effective
security strategies.
How Do Honeypots
Work?
Honeypots are designed to act as bait for cybercriminals.
They are usually set up to mimic real systems, applications, or devices that
may contain sensitive data or valuable assets. However, unlike genuine systems,
honeypots are isolated and monitored closely to detect any suspicious activity.
Here’s how a honeypot typically works:
Why Honeypots are
Important for Cybersecurity?
CODELANCER’s
Honeypot Services
CODELANCER CYBER SECURITY AND FORENSIC PRIVATE LIMITED
offers Honeypot Services designed to enhance your organization's
security defenses by providing real-time insights into cyber threats and attack
behavior. Our honeypot services are tailored to meet the unique needs of each
client, and our team of experts ensures that honeypots are set up and monitored
with precision.
Here’s how CODELANCER’s Honeypot Services can benefit
your organization:
1. Custom Honeypot
Deployment
We customize the deployment of honeypots based on your
organization’s infrastructure and risk profile. Our team works with you to
design honeypots that replicate the types of systems or assets most likely to
be targeted by attackers, ensuring maximum effectiveness.
2. Continuous
Monitoring and Threat Detection
Once deployed, our honeypots are continuously monitored
by our expert security team. We ensure that all interactions with the honeypots
are logged and analyzed in real-time, enabling swift identification of
potential threats and malicious activity.
3. Intelligent
Threat Intelligence
CODELANCER’s honeypot services provide you with
actionable threat intelligence that can be used to strengthen your overall
cybersecurity posture. We analyze the data captured from honeypot interactions
and provide you with detailed reports on attack methods, malware, and
exploitation techniques.
4. Forensic
Investigation and Reporting
In the event of an attempted attack on your honeypot,
CODELANCER conducts thorough forensic investigations to trace the origin,
methods, and impact of the attack. This detailed analysis helps businesses
understand the motivations behind the attack and the potential risks to their
real systems.
5. Proactive
Defense Strategies
The insights gained from our honeypot services are used
to develop proactive defense strategies for your organization. This includes
patching vulnerabilities, strengthening access controls, and enhancing threat
detection measures to prevent future attacks.
Why Choose
CODELANCER for Honeypot Services?
Conclusion
In the constantly evolving world of cyber threats,
honeypots provide an innovative and effective way to detect, analyze, and
respond to attacks before they compromise your critical systems. By leveraging
CODELANCER’s Honeypot Services, organizations can gain valuable insights into
attacker tactics and improve their defenses against emerging threats.
If you're looking to stay one step ahead of
cybercriminals and protect your valuable assets, CODELANCER’s Honeypot Services
are the perfect solution. Contact us today to learn how our honeypot technology
can help strengthen your cybersecurity strategy and provide proactive protection
for your business.
Copyright 2017-2025 All Rights Reserved to CODELANCER CYBER SECURITY
Secured by CFRM