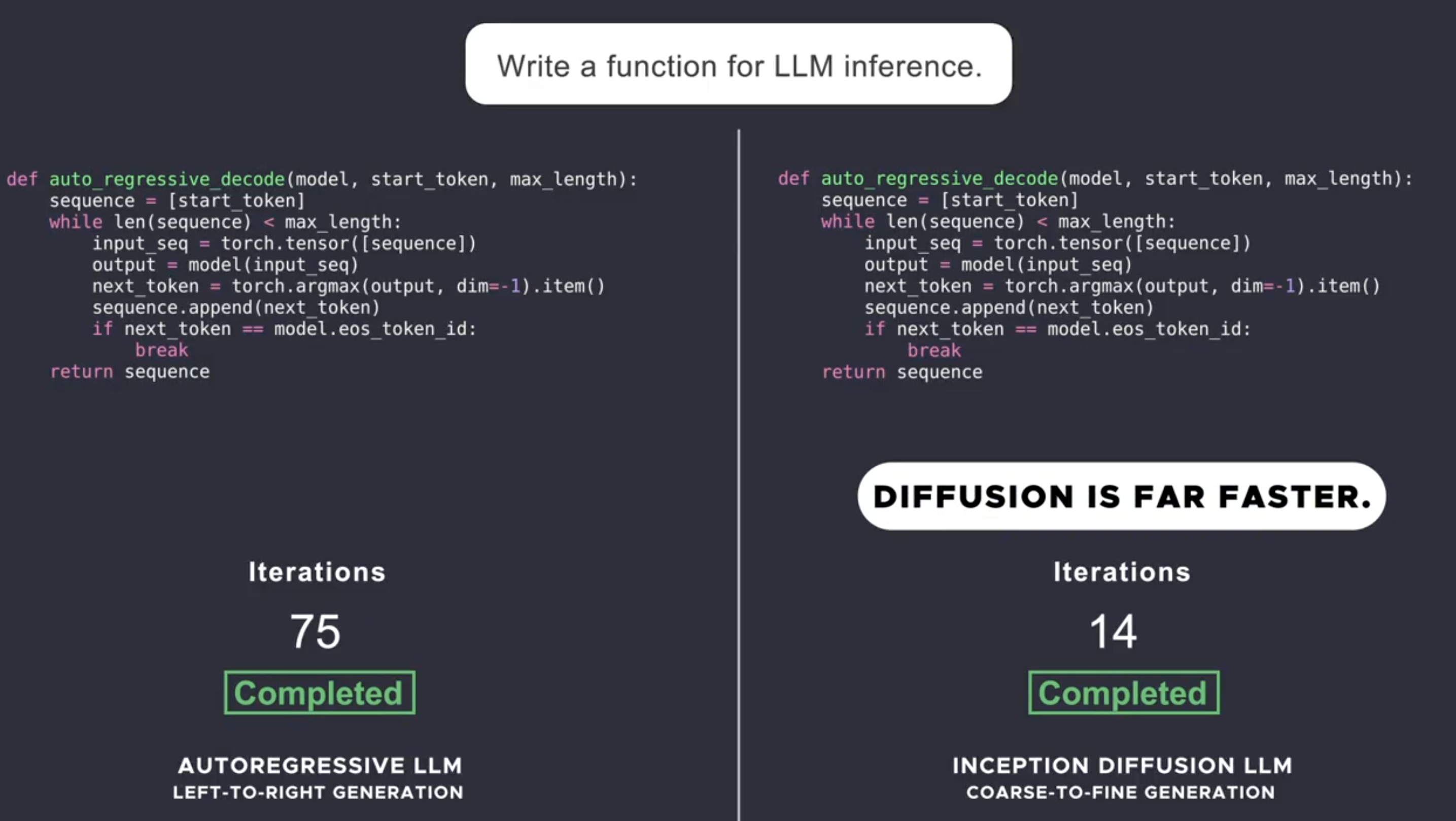
Financial Fraud Analysis In Ghatkoper
inancial fraud in Ghatkopar, like in other urban areas, involves various forms of criminal activity, including payment fraud, account takeovers, identity theft, and investment scams. Businesses and individuals in Ghatkopar face increasing risks due to the digitalization of financial transactions. To mitigate these risks, organizations need to implement robust security measures, such as two-factor authentication, regular audits, data encryption, and fraud detection software. Employee training and awareness are crucial, as is having an incident response plan to recover from potential fraud.

In today’s interconnected world, financial fraud has become a significant threat to businesses and individuals alike. From unauthorized transactions to identity theft, understanding these risks and implementing effective protection measures is crucial for safeguarding financial assets and maintaining trust. This guide outlines actionable steps to protect your organization from these pervasive financial threats.
Types of Financial Fraud
- Payment Fraud: Involves unauthorized transactions or fraudulent payments using stolen credit cards or bank account details.
- Account Takeover: When cybercriminals gain access to an individual’s or business's financial accounts and conduct fraudulent activities.
- Identity Theft: The use of personal or business identity information to commit fraud, often for financial gain.
- Invoice Fraud: A type of social engineering where attackers impersonate vendors and manipulate businesses into paying fraudulent invoices.
- Investment Fraud: Fraudulent schemes that involve deceptive investment opportunities, often leading to significant financial loss.
Key Strategies for Protection
-
Implement Strong Financial Controls
- Two-Factor Authentication (2FA): Enforce two-factor authentication on all financial transactions to prevent unauthorized access.
- Account Monitoring: Set up alerts for unusual or high-value transactions to quickly detect fraud.
- Access Controls: Limit access to financial systems and accounts based on the principle of least privilege.
- Segregation of Duties: Ensure that no single person has control over all aspects of financial transactions, from initiation to approval.
-
Data Encryption and Protection
- Encrypt Sensitive Information: Use encryption methods to protect sensitive financial data during transmission and storage.
- Secure Payment Gateways: Employ secure and trusted payment processors for online transactions to minimize fraud risks.
- Data Masking: Apply data masking techniques to protect credit card numbers, bank details, and personal information.
-
Conduct Regular Audits and Risk Assessments
- Internal Audits: Conduct regular audits to identify any financial discrepancies and prevent fraudulent activities.
- Third-Party Risk Management: Assess and monitor the security practices of third-party vendors involved in financial transactions.
- Continuous Risk Assessment: Continuously evaluate and adapt financial fraud protection measures in response to emerging threats.
-
Employee Training and Awareness
- Fraud Awareness Programs: Educate employees on recognizing phishing scams, fake invoices, and other fraudulent activities.
- Regular Simulations: Conduct simulated fraud attempts to test employees' ability to recognize and report fraudulent activity.
- Whistleblower Programs: Implement a secure and anonymous way for employees to report suspected fraud.
-
Leverage Financial Fraud Detection Tools
- Fraud Detection Software: Implement AI-based fraud detection tools that analyze transaction patterns and flag anomalies in real time.
- Behavioral Analytics: Use behavioral analytics to detect irregularities in transaction patterns that may indicate fraudulent activity.
- Machine Learning Models: Deploy machine learning algorithms to continuously learn and adapt to new fraud tactics.
-
Incident Response and Recovery
- Fraud Investigation and Mitigation: Set up protocols for investigating suspected fraud and mitigating any financial loss quickly.
- Communication Plans: Develop a communication strategy for informing stakeholders about a financial fraud incident.
- Fraud Recovery: Have a recovery plan in place to recover stolen funds or mitigate losses through insurance or financial institutions.
How Codelancer Cybersecurity Can Help
At Codelancer Cybersecurity, we specialize in providing comprehensive financial fraud protection services. Our solutions include:
- Fraud Risk Assessment: We conduct thorough assessments to identify and mitigate fraud risks specific to your financial operations.
- Tailored Security Solutions: Our team designs customized fraud prevention measures, including advanced detection tools and secure payment systems.
- Employee Training Programs: We offer targeted fraud awareness training to ensure your employees are equipped to recognize and report fraud.
- Incident Response Support: Our experts assist with investigating fraud incidents and minimizing financial damage.
- Continuous Monitoring: We provide real-time fraud monitoring to detect and prevent suspicious activities before they escalate.
Conclusion
Protecting your organization from financial fraud requires a multi-layered approach, involving robust financial controls, encryption, continuous monitoring, employee training, and a strong incident response plan. By implementing these strategies, you can significantly reduce the risk of financial fraud and safeguard your company’s financial integrity.
For more information and personalized cybersecurity solutions, visit Codelancer Cybersecurity & Forensics.
What's Your Reaction?