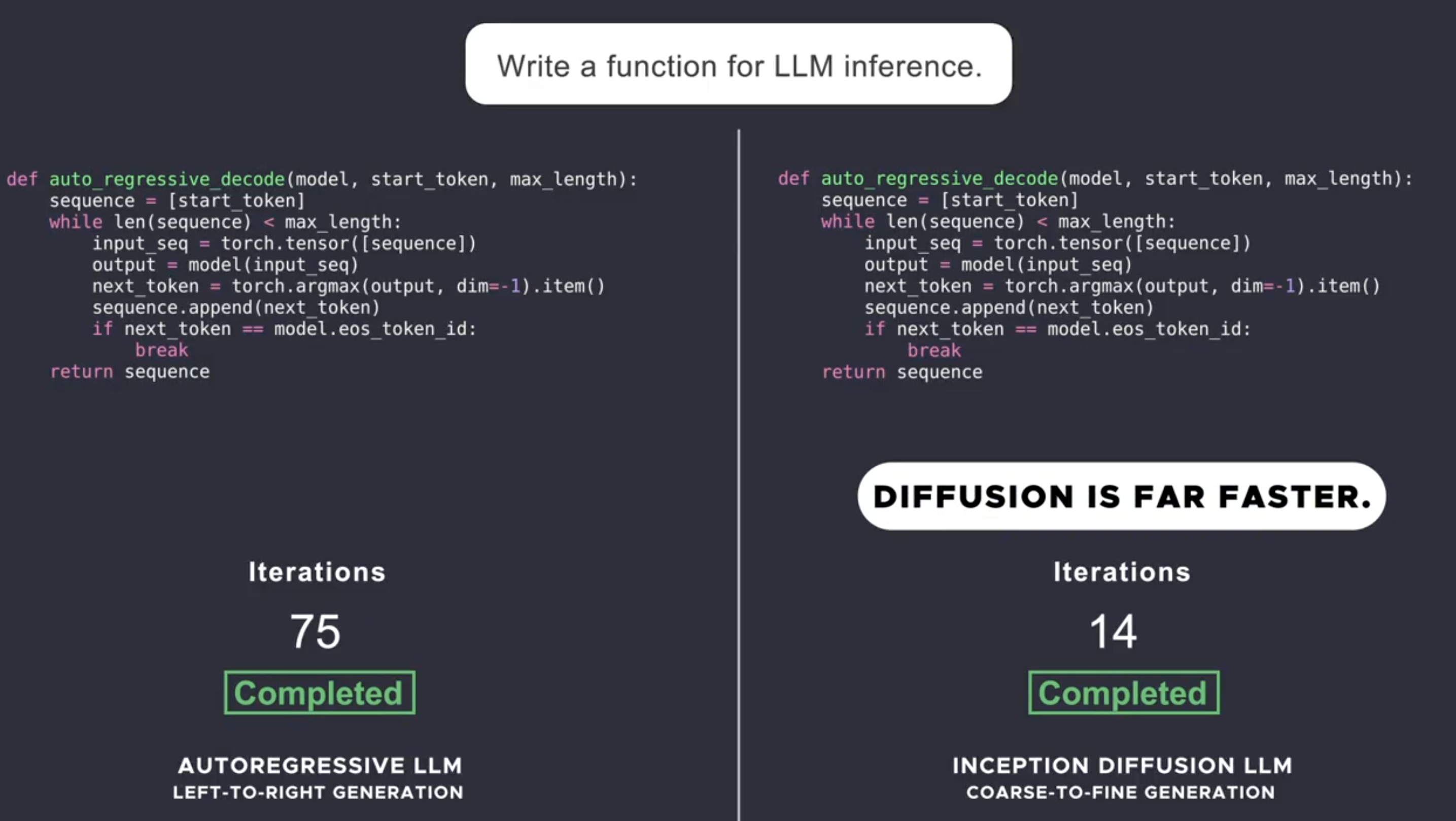
Understanding the Impact of Brute Force Attacks on Cybersecurity in Mumbai
Brute force attacks pose a significant cybersecurity threat, exploiting weak passwords to gain unauthorized access to systems and data. Codelancer offers expert solutions to help businesses prevent and mitigate these attacks through strong password policies, two-factor authentication, encryption, and advanced threat detection. Protect your organization from brute force attacks with Codelancer's cybersecurity expertise.

Brute force attacks are one of the most common and dangerous cyber threats, exploiting weak or easily guessed passwords to gain unauthorized access to systems, networks, or data. These attacks can cause serious security breaches, resulting in data theft, financial loss, and reputation damage. Understanding how brute force attacks work and how to protect against them is essential for organizations seeking to strengthen their cybersecurity defenses. Codelancer is here to guide you through the intricacies of brute force attacks and how to prevent them.
Why Brute Force Attacks Are a Growing Threat in Cybersecurity
- Exploitation of Weak Passwords: Brute force attacks rely on the methodical guessing of passwords by trying all possible combinations. This makes systems with weak or common passwords vulnerable to attack.
- Automated Tools and Speed: Attackers use automated tools that can rapidly try billions of combinations in a short period, making brute force attacks more effective and harder to defend against.
- Business Impact: Successful brute force attacks can lead to unauthorized access to sensitive information, service disruptions, and data breaches, damaging an organization’s reputation and financial stability.
Key Features of Brute Force Attacks in Cybersecurity
- Password Cracking: Brute force attacks typically involve trying every possible password combination until the correct one is found, using dictionary lists or randomized characters.
- Distributed Attacks: Attackers may use botnets or distributed denial-of-service (DDoS) techniques to amplify brute force attacks, making them harder to mitigate.
- Credential Stuffing: In some cases, brute force attacks are combined with credential stuffing, where previously leaked usernames and passwords are used to gain access to multiple systems.
- Layered Attacks: Hackers may layer brute force attacks with other techniques, such as phishing or social engineering, to gather information before launching the attack.
How Brute Force Attacks Affect Cybersecurity
- Data Breaches: Brute force attacks can compromise sensitive data, leading to potential data breaches. The stolen data can be used for identity theft, fraud, or sold on the dark web.
- Loss of Reputation: When a brute force attack is successful, it damages the credibility and trust of an organization, especially if customer data is exposed.
- Increased Security Costs: Organizations affected by brute force attacks may face significant costs in securing their systems, compensating for data loss, and recovering from the breach.
Preventing Brute Force Attacks: Best Practices for Cybersecurity
- Strong Password Policies: Encourage the use of complex passwords that include a combination of letters, numbers, and symbols. Password length and unpredictability are key to preventing brute force attacks.
- Two-Factor Authentication (2FA): Implement 2FA to add an extra layer of protection, making it harder for attackers to gain access even if they crack the password.
- Account Lockout Mechanisms: Set up account lockout policies that temporarily disable accounts after a set number of incorrect login attempts, reducing the success rate of brute force attacks.
- Encryption: Encrypt sensitive data to ensure that even if attackers gain access, the information remains unreadable without the proper decryption keys.
- Rate Limiting: Implement rate limiting on login attempts to slow down the brute force process and give defenders more time to react to an ongoing attack.
Why Organizations Need Expertise in Defending Against Brute Force Attacks
As brute force techniques continue to evolve and grow in sophistication, organizations must rely on cybersecurity experts to mitigate these risks. Here's why Codelancer can help:
- Expert Analysis: Our cybersecurity experts can assess your organization's current security posture, identifying vulnerabilities that may make you a target for brute force attacks.
- Advanced Threat Detection: We utilize state-of-the-art tools and technologies to detect and block brute force attempts before they compromise your systems.
- Incident Response: Should a brute force attack occur, Codelancer provides rapid response services to contain the threat, assess the damage, and restore normal operations.
- Ongoing Security: We offer ongoing security services to ensure that your systems are continuously protected against brute force and other emerging cyber threats.
Protect Your Organization from Brute Force Attacks with Codelancer
Brute force attacks represent a serious cybersecurity threat, but with the right defenses in place, organizations can mitigate the risks and protect their assets. Codelancer offers expert cybersecurity solutions to help businesses stay one step ahead of attackers. From proactive threat detection to rapid response and incident management, we ensure your systems remain secure.
For more information or to inquire about our services, visit our website or reach out to us directly. Protect your organization from brute force attacks with expert cybersecurity solutions from Codelancer.
What's Your Reaction?